Featured
Table of Contents
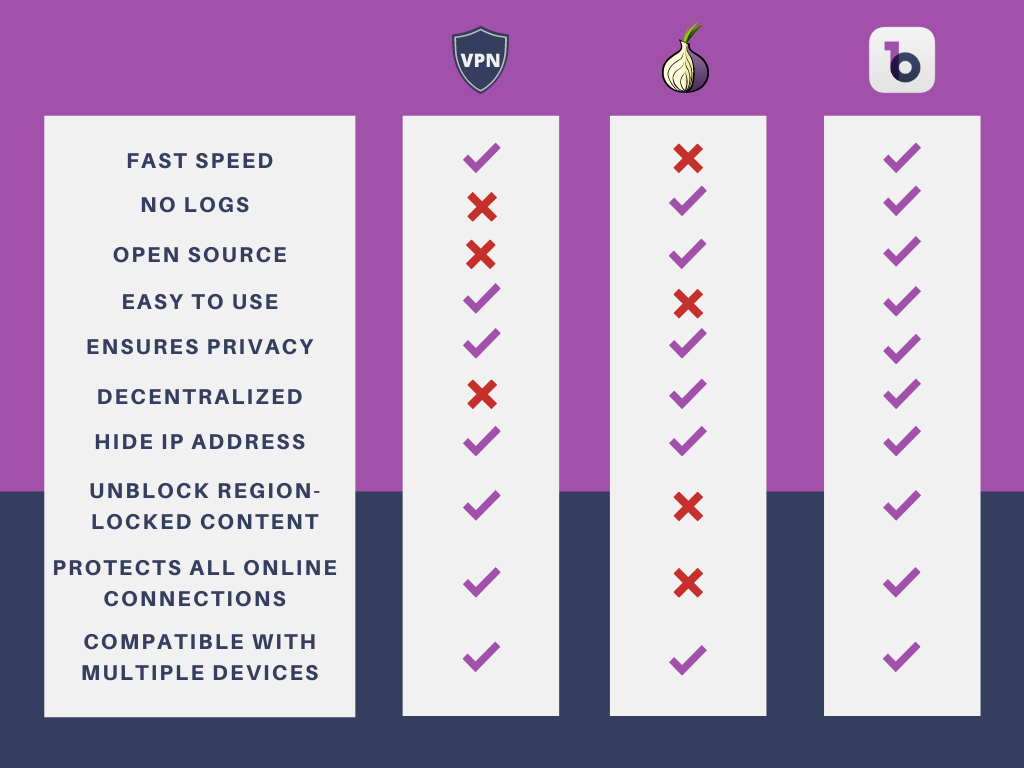
Tor Vs Vpn—what Is The Difference?
Do you ever question who can see your internet traffic while surfing the web? If so, you're not alone. 63% of customers are worried more than ever about their online privacy. Whether you watch out for your internet service supplier, nosy websites, or even worse, hackers, many individuals are taking additional preventative measures to protect their personal privacy online.
By utilizing these tools, web users can use the web with improved peace of mind. The middle node then eliminates the second layer of encryption and sends your demand to the exit node. The exit node eliminates the last layer of encryption, enabling it to see your demand, although it will be not able to identify who requested it.
When To Use Tor Or A Vpn - Privadovpn
The only method someone can identify your activity is if they occurred to maintain both of the arbitrarily picked guard and exit nodes, which is highly not likely. While utilizing the Tor browser has its benefits, there are benefits and disadvantages when it concerns using Tor over a conventional internet browser like Safari or Google Chrome.
Pros of using the Tor internet browser: Free and easy to download: Thanks to various confidential volunteers, users can quickly download and use the Tor internet browser totally free. Tough to shut down: The Tor network is run by countless volunteers all over the world, making it extremely difficult for a single entity to shut it down.
Bypass censorship: If you remain in a country with stringent censorship, the Tor browser will enable you to bypass censorship and go to obstructed sites. Access to the dark web: With the Tor browser, you have the ability to access websites on the dark web. These sites are also called onion sites and can just be visited using the Tor web browser.
Vpn Vs Tor — Which Is Better?
Node vulnerability: Because the Tor internet browser helps make your identity anonymous, it does not bother encrypting your information after it leaves the exit node. This makes it possible for somebody monitoring your connection to see your traffic data, even if they don't know who it belongs to. Even with its pros and cons, there are specific circumstances in which utilizing the Tor browser might be your finest choice.
Now that you know the advantages and downsides of using Tor, you might be questioning when you ought to use it. Tor is best for: Confidential web browsing Accessing the dark web Untraceable interaction If your primary priority is remaining confidential online or you wish to access the dark web, then using the Tor web browser may be your best option.
This allows VPN users to travel the web independently and anonymously, no matter the internet connection. A VPN will likewise conceal your IP address and encrypt your web traffic. So, how does a VPN work? Your web traffic is encrypted and sent to a remote server to camouflage your IP address.
Vpns, Tor, I2p — How Does Nym Compare?
This exact same procedure takes place with the data returning to your device. Simply like using the Tor web browser, VPNs aren't ideal.
Follow along to learn when utilizing a VPN is your finest choice. After finding out more about VPNs, you may be wondering when to use one. A VPN is finest for: If you live someplace with rigorous internet censorship and often discover yourself using public Wi-Fi connections, investing in a VPN service might be a great option.
Prior to choosing a VPN or Tor, follow along to find out more about the essential distinctions. One big distinction between a VPN and Tor is how they're handled. A VPN is a centralized service, suggesting the VPN service provider is the sole authority, handling all servers and connections. For the most part, this is a private company.
Tor Vs Vpn: What's The Difference And Which Is Safer?
On the other hand, Tor is entirely decentralized, and none of its servers are controlled by a single entity. Instead, the decentralized network counts on its worldwide network of private volunteers. Since of this, it is far more difficult for somebody to trace your data or shut down the network.

Most VPNs direct your web traffic through a single server before it reaches its desired destination. This is referred to as a single-hop VPN. On the other hand, the Tor web browser paths your web traffic through three random nodes. This complicated procedure makes your data naturally difficult to trace. When it comes to picking a VPN, you'll have many alternatives to pick from.
This grants you all of the privacy benefits of the Tor network and extra IP address protection from your VPN, avoiding your ISP from knowing that you use Tor and keeping any Tor node from seeing your IP address. Tor then VPN: Beginning with the Tor network is a challenging procedure and may not be supported by all VPN companies.
Tor Vs Vpn Vs Proxy: Which Should I Use In 2023
When you use a VPN, you need to rely on the VPN service company. Because each Tor node only knows the identity of the server prior to it, it is difficult for anybody to reverse engineer your connection's route through the Onion network. Tor likewise lets you gain access to a variety of unlisted sites with the.


VPNs don't need the exact same level of technical proficiency as utilizing Tor does. You need to still make sure to pick a trustworthy, zero-logs VPN service provider that does not to leak user data. If you're short on time, here are some quick responses to typical questions asked about Tor vs.This makes VPNs the preferred approach of bypassing geo-restrictions. The Dark Web (. onion websites) are only available through the Tor browser. Users can opt to utilize a VPN with Tor for an extra layer of security.
Latest Posts
Business Vpn: What Is It And Which One Should You Consider?
What Is A Business Vpn? Understand Its Uses And ...
Business Vpn For Small & Enterprise Companies